“An IP address (short for Internet Protocol address) is used to identify computers on the Internet. It works like a return address would on a piece of mail. When your computer or device sends a request, like a search on Google, it tags the request with your IP address. You can find an approximate location of the device through its IP address.”
Now it is obvious that a user’s ISP location can easily be identified from their IP address and this is a publicly available feature mainly utilized to identify the end point’s country of origin.
For this article, I am willing to compromise my “approximate location” (edit: that is entirely different from the ISP location are more towards my current geolocation, which is visible from the screenshots below)from a cafe because you can anyway get this information. Thanks to google :)
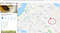
I did a quick lookup on my IP address location and here is how it looks

Notice the identified latitude and longitude, marking it on google map (below)you can see the distance of this location from my original point of access.

Great, now let us look at what Google does. We first turn on our Geolocation (allow location) on our Browser and write a quick javascript to get geolocation.

This “Geo Location” got directly from the browser GeoLocation API can show you how close this is to my original location (Notice, the identified location is still not in the circle)

But wait. For this I basically had to turn on my location. Have I become another fs0c131y that reports these kinds of information. Fortunately not! (Oof! That below the belt attack. #ForTehLulz)
HOWEVER, now I noticed that when I opened google maps with my “allow location” turned off, it automatically focused on the region where I resided. Here is where during a discussion, Smith gave me the idea to look into Google APIs.
So researching further, I came across this interesting API on Google APIs https://developers.google.com/maps/documentation/geolocation/intro
Quick Notes from Geolocation Docs:
a. Either give it Wi-Fi or Cell Tower data or the API returns it’s response based on your IP Address
b. API responds with location and accuracy that mobile client can detect
c. Response: {“latitude”:””, “longitude”:””, “accuracy”:””}
I actually have no idea how (edit: because I don’t want to hypothesize this without any factual evidence)location services got me a more accurate result after several attempts but here is what I did. After allowing google maps once and turning on my “Allow Location” and reloading multiple times on the browser (edit: because while testing code at times you need to reload the browser), I noticed the Browser Geolocation output was more accurate (Remember the location initially revealed was not in the circle).


The POC
This is where you turn off allow location and identify yourself with the Google API and be ready to get amazed. 2.1km Accuracy? Lol. And my fish fry lunch!


The Cliche Fun and Profit
Obviously now that we got this interesting API giving out user locations, I had to identify the aspects of fun and profit with this AP
Observe above, the user location accuracy can also sometimes be 561km, 3km, etc. Only after this test did I really understand how Google was storing your location and providing it to 3rd parties (see Conclusion for my inferences). Mobile internet users, you guys seem to be super safe if people are travelling around with a specific IP address.
Edit: Based on some clarification requests, I added the POC code on how a third party web application can capture user details.

Another area that one can explore is exploiting user endpoint script parsing. For example, I embedded the javascript on a HTML and uploaded it on html2pdf.comonly to get the server location on my server and BAM!

(Location compromising SSRF! However, this is obviously not a security issue. Might have been a privacy issue for the server, which I don’t believe is in this case.)
Le Conclusion
You can’t fight Google’s influence on your life. If you are not utilizing safeguards like a VPN, you are basically very bold on the current internet. Everyone is collecting your data.
What Google does is it stores the coordinates of your IP address if you “Allow Location” on your device or your browser. However, if you are utilizing a ISP with Dynamic IP allocation, be prepared that someone near you might get this IP address and give out their coordinates. Google approximates these location coordinates and provides a precise location coordinate to anyone any uses “Geo Location API”.
(edit)Here are a few steps that could help for this specific case:
- Use a Virtual Private Network (Spoofed IP will result in Google to give location information of the spoofed IP address or whatever it stored for it)
- Feed wrong information to Google (Fake GPS). When I was at 36C3, pre-conference the IP address resolved accurate geolocation with the help of GoogleAPI. This was because individuals around the area basically shared their location coordinates with Google while using the Wi-Fi. As the conference came, there were multiple GPS Spoofed signals broadcast around the area. This resulted in Google API to locate the IP address to the spoofed coordinates rather than the real one.
Also remember: Your privacy is your responsibility!

On behalf of Google for the Google haters, I understand that there is a slight distortion of the original location (location approximate value). This is something that Google stands by to consider it not privacy violation. The closest I have tracked myself to a locations where the accuracy mentioned were down to 700 to 800 meters while the location was about a block away. And at times the accuracy mentioned 2km but the GeoLocation showed the location of the building next to my location.
If you think there is a privacy violation by Google by exposing such a accessible API, please let me know.








Comments
Post a Comment